Resource Cleanup
Detect and delete orphaned resources above a certain age.
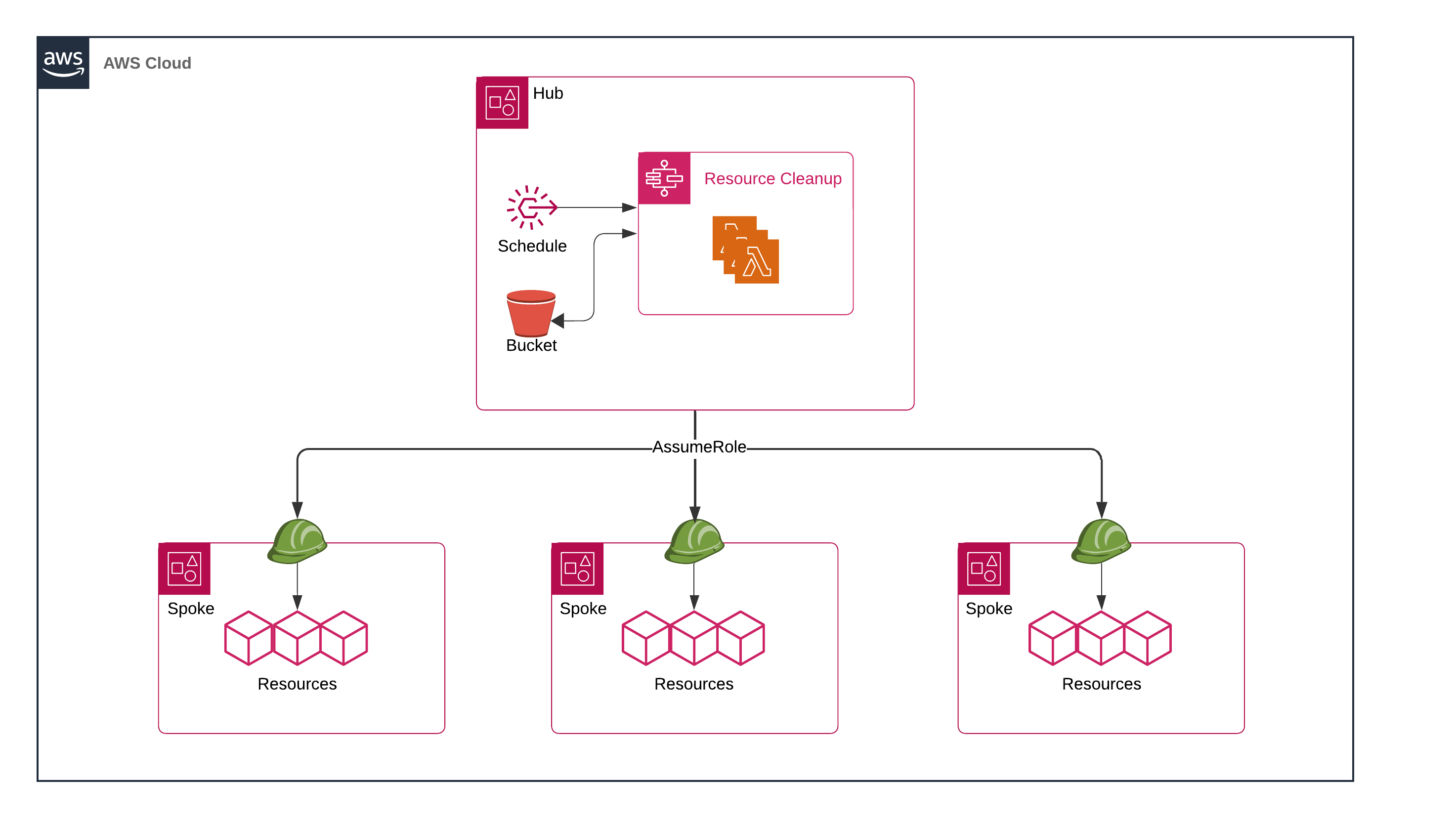
Overview
This workflow follows a hub-and-spoke model where components are deployed to a service (hub) account and a role is deployed to each serviced (spoke) account.
Operation
The workflow will assume a role in each serviced account and perform the following actions in each configured region:
- Discover resources that don’t have exclusion tags
- Evaluate the age and state of the discovered resources
- Retrieve resources scheduled for deletion from S3
- Remove resources from S3 that are not discovered in current run
- Retrieve resources ready to delete from S3
- Derived from S3 object last modified date and
wait_before_delete_days
- Derived from S3 object last modified date and
- Delete resources that are discovered in current run and ready for deletion
- Schedule newly detected resources for deletion by uploading to S3
The workflow is scheduled to run once a day through an EventBridge Rule.
Adjustable by passing a custom schedule to the schedule module.
Workflow logs can be found in CloudWatch Logs.
At the moment there isn’t any support for producing a notification in the event of a resource being deleted. You can request this by emailing dimitar@avtomat.io.
Supported resource types
EC2 Images
- Delete images older than the threshold
- Delete underlying snapshots comprising the image
- Do not target images managed by AWS Backup
- Do not target images with exclusion tags
EC2 Snapshots
- Delete snapshots older than the threshold
- Do not target snapshots managed by AWS Backup
- Do not target snapshots with exclusion tags
EC2 Volumes
- Delete volumes in detached state for a period longer than threshold
- Create a snapshot before deleting the volume
- Do not target volumes with exclusion tags
- Maximum threshold supported: 90 days
- Log a warning and skip volumes for which CloudTrail event cannot be found
EC2 Instances - COMING SOON
- Delete instances in stopped state for a period longer than threshold
- Create an image before deleting the instance
- Do not target instances with exclusion tags
- Maximum threshold supported: 90 days
- Log a warning and skip instances for which CloudTrail event cannot be found
Configuration
This workflow is configured through config.json. Each supported resource type has its own configuration section.
Schema
accounts- List of account IDs to be scannedvars- Workflow variablesregions- List of regions to be scanned in each accountexclude_tags- Tags that exclude resources from being scannedthreshold_days- Age threshold for resources to be scheduled for deletionwait_before_delete_days- Grace period before resources that are scheduled for deletion are actually deletedcutoff_date- Date before which resources are not scanned (Only applies toec2-imagesandec2-snapshots)bucket_name- S3 bucket name for storing resources that are scheduled for deletion
To exclude a resource type from being scanned, pass an empty accounts.
{
"ec2-images": {
"accounts": []
}
}
Requirements
- Terraform
- AWS CLI
- avtomat-aws
- Collection must exist as a Lambda Layer in the hub account before deploying this workflow
Components
| Resource | Amount | Description |
|---|---|---|
| EventBridge Rule | 1 | To schedule the workflow. |
| S3 Bucket | 1 | To store resources scheduled for deletion. |
| Step Function | 1 | To orchestrate the lambda functions. |
| Lambda Function | 3 | Source code for the workflow. Lambda per resource type. |
| CloudWatch Log Group | 3 | Workflow logs. Log group per lambda. |
| IAM Role | 5 | x3 Lambda function role. x1 EventBridge role for rule to start step function. x1 Step function role to start lambda functions. |
| IAM Role Policy | 5 | x3 Policy for lambda function role. x1 Policy for eventbridge role. x1 Policy for step function role. |
| IAM Service Role | X | Service role assumed by the workflow. Deployed to hub and spoke accounts. |
| IAM Service Role Policy | X | Policy for service role. |
Deployment
This workflow can be deployed through Terraform.
Read Deploy to get started.