Access Key Control
Detect IAM access keys over a certain age and disable them.
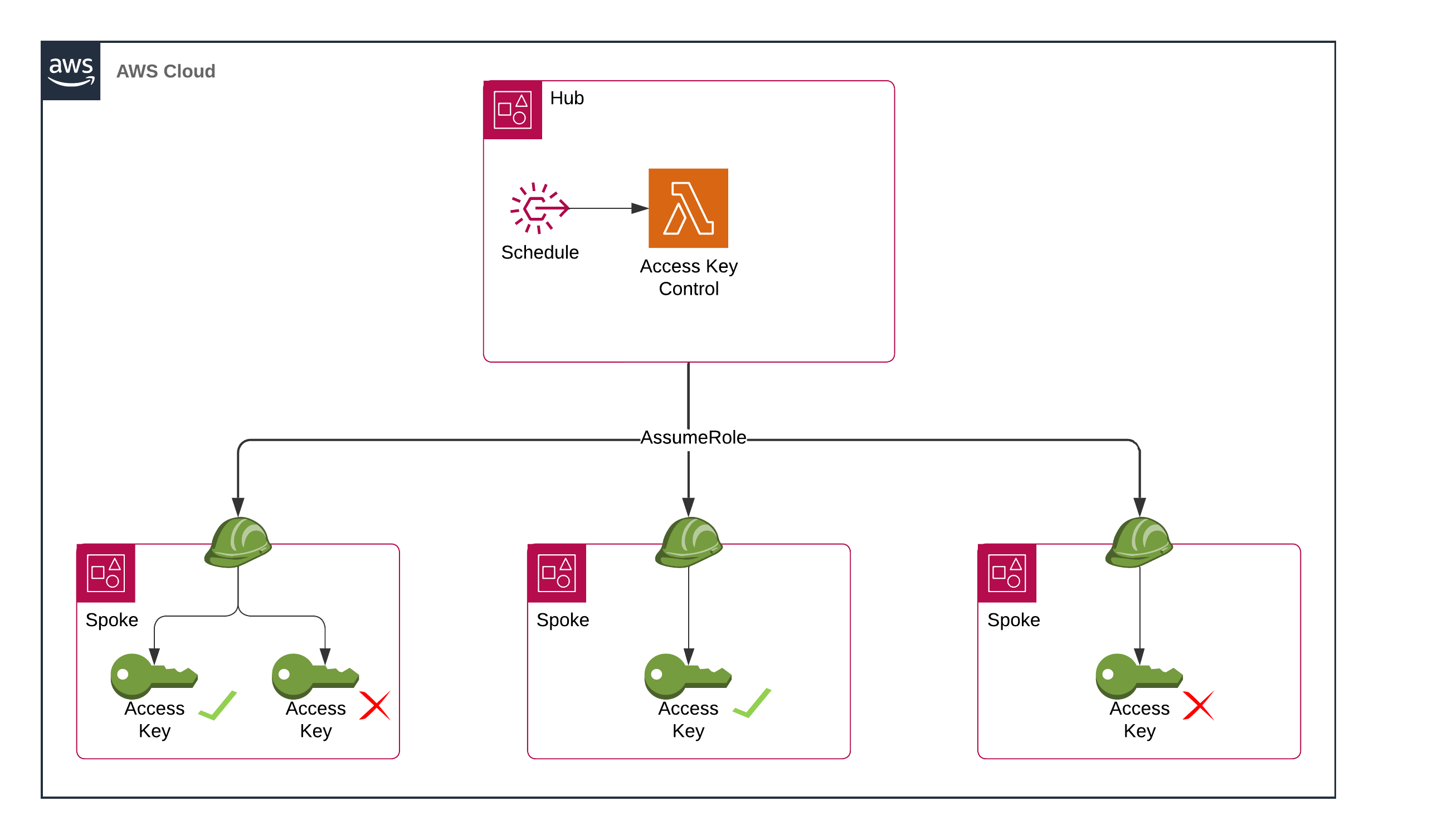
Overview
This workflow follows a hub-and-spoke model where components are deployed to a service (hub) account and a role is deployed to each serviced (spoke) account.
Operation
The workflow will assume a role in each serviced account and perform the following actions:
- Discover IAM access keys over a certain age
- Disable the discovered access keys
The workflow is scheduled to run once a day through an EventBridge Rule.
Adjustable by passing a custom schedule to the core module.
Workflow logs can be found in CloudWatch Logs.
At the moment there isn’t any support for producing a notification in the event of a key being disabled. You can request this by emailing dimitar@avtomat.io.
Requirements
- Terraform
- AWS CLI
- avtomat-aws
- Collection must exist as a Lambda Layer in the hub account before deploying this workflow
Components
| Resource | Amount | Description |
|---|---|---|
| EventBridge Rule | 1 | To schedule the workflow. |
| Lambda Function | 1 | Source code for the workflow. |
| Lambda Function Permission | 1 | Permission allowing eventbridge rule to invoke lambda function. |
| CloudWatch Log Group | 1 | Workflow logs. |
| IAM Role | 1 | Basic lambda function permissions. |
| IAM Role Policy | 1 | Policy for lambda function role. |
| IAM Service Role | X | Service role assumed by the workflow. Deployed to hub and spoke accounts. |
| IAM Service Role Policy | X | Policy for service role. |
Deployment
This workflow can be deployed through Terraform.
Read Deploy to get started.